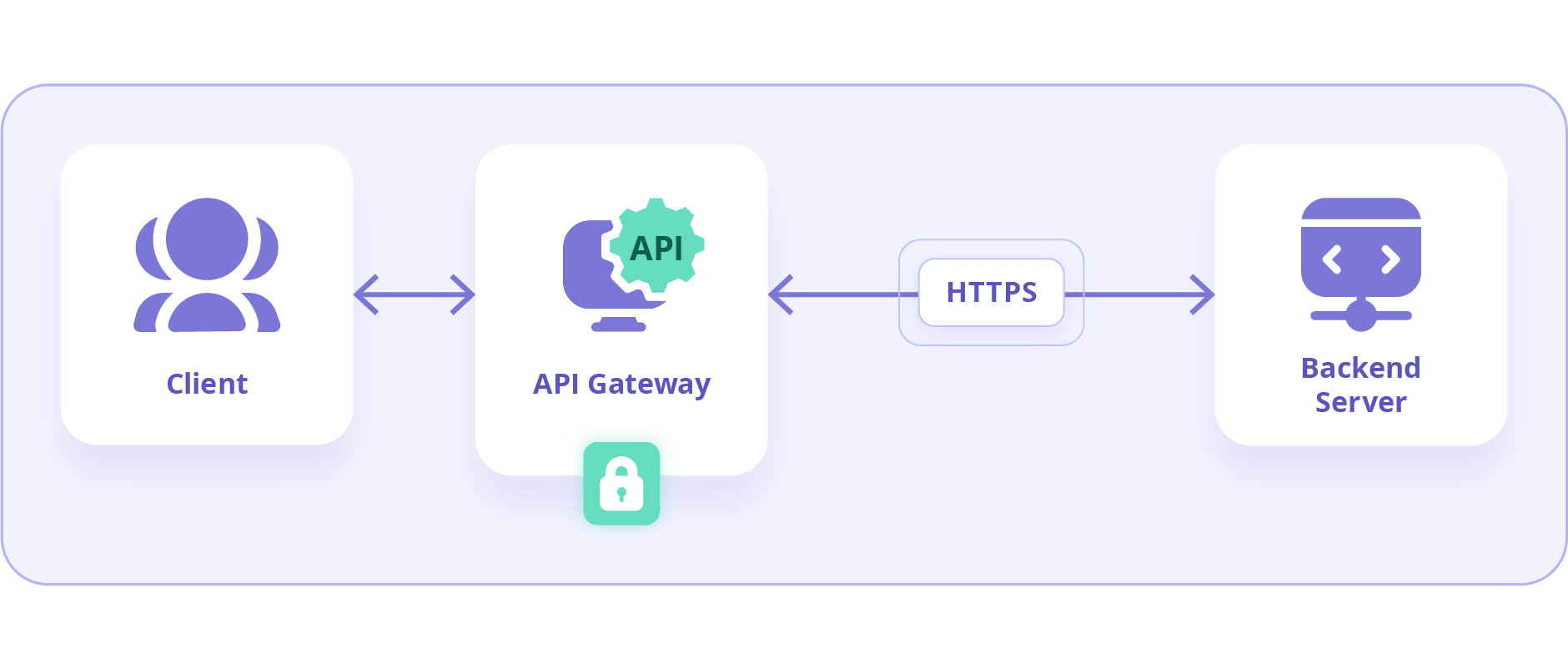
API security is an essential aspect of modern API security software architecture. It provides a brilliant way for different applications to communicate with each other. The API Gateway acts as a security barrier between the client and microservices in the backend, ensuring that sensitive data is protected and only authorized clients can access the microservices.
In this blog, we will delve into the concept of API Gateway and its role in ensuring security for microservices. We will also discuss the benefits of API Gateway security and the best API security methods for securing API Gateway in 2025. Whether you’re a software developer, DevOps engineer, or just someone interested in learning about API security methods, this blog will provide you with valuable insights and tips to improve the security of your APIs.
Evolving attack vectors: DDoS, credential stuffing, injection attacks
Modern APIs face escalating threats like DDoS attacks that overwhelm systems, credential stuffing that exploits leaked passwords, and injection attacks (such as SQL injection) targeting vulnerable input fields. API gateways defend against these by enforcing rate limits, monitoring for unusual behavior, and validating all incoming data to block malicious payloads before they reach backend services.
API Gateway Security Best Practices for 2025
API security best practices or API security methods are necessary to secure APIs and protect sensitive data from malicious actors, breaches, and other API security risks.
What is an API Gateway?
An API Gateway serves as a mediator between a client and the microservices in its backend. Its role encompasses routing, protocol translation, composition, and other functions. These functions allow multiple clients to access the microservices in the backend. Moreover, securing api gateway is essential for securing the underlying infrastructure and communication of the API and connected microservices.
The Role of API Gateways in Ensuring Security
API Gateways provide a strategic point to implement robust security measures such as API Gateway security groups and API management security, crucial for protecting sensitive data from unauthorized access. These gateways ensure that only secure API calls are processed, significantly reducing the potential attack vectors.
Here are some of the best practices for API Gateway security, also known as an API Gateway security checklist:
Use Modern Authentication Methods
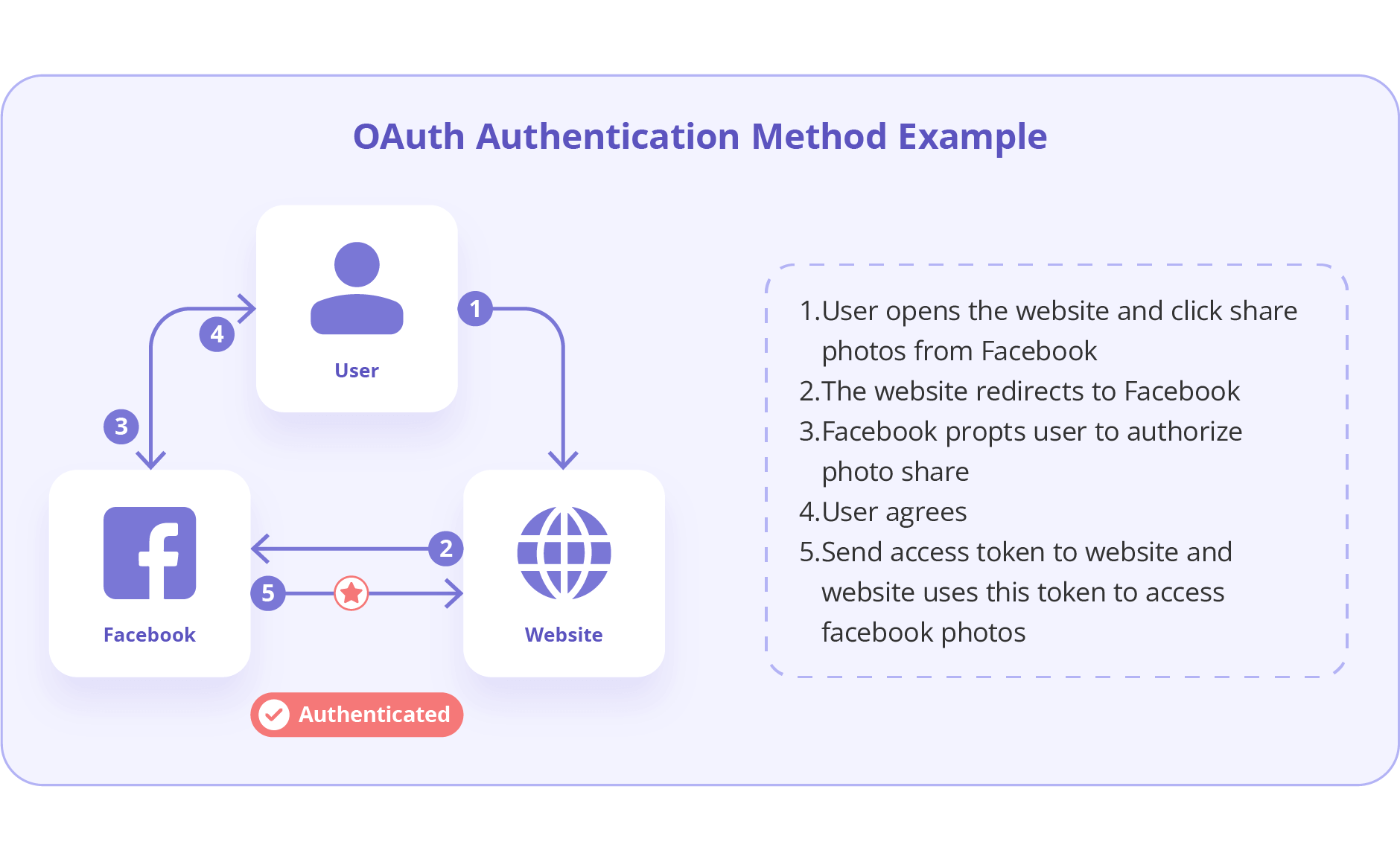
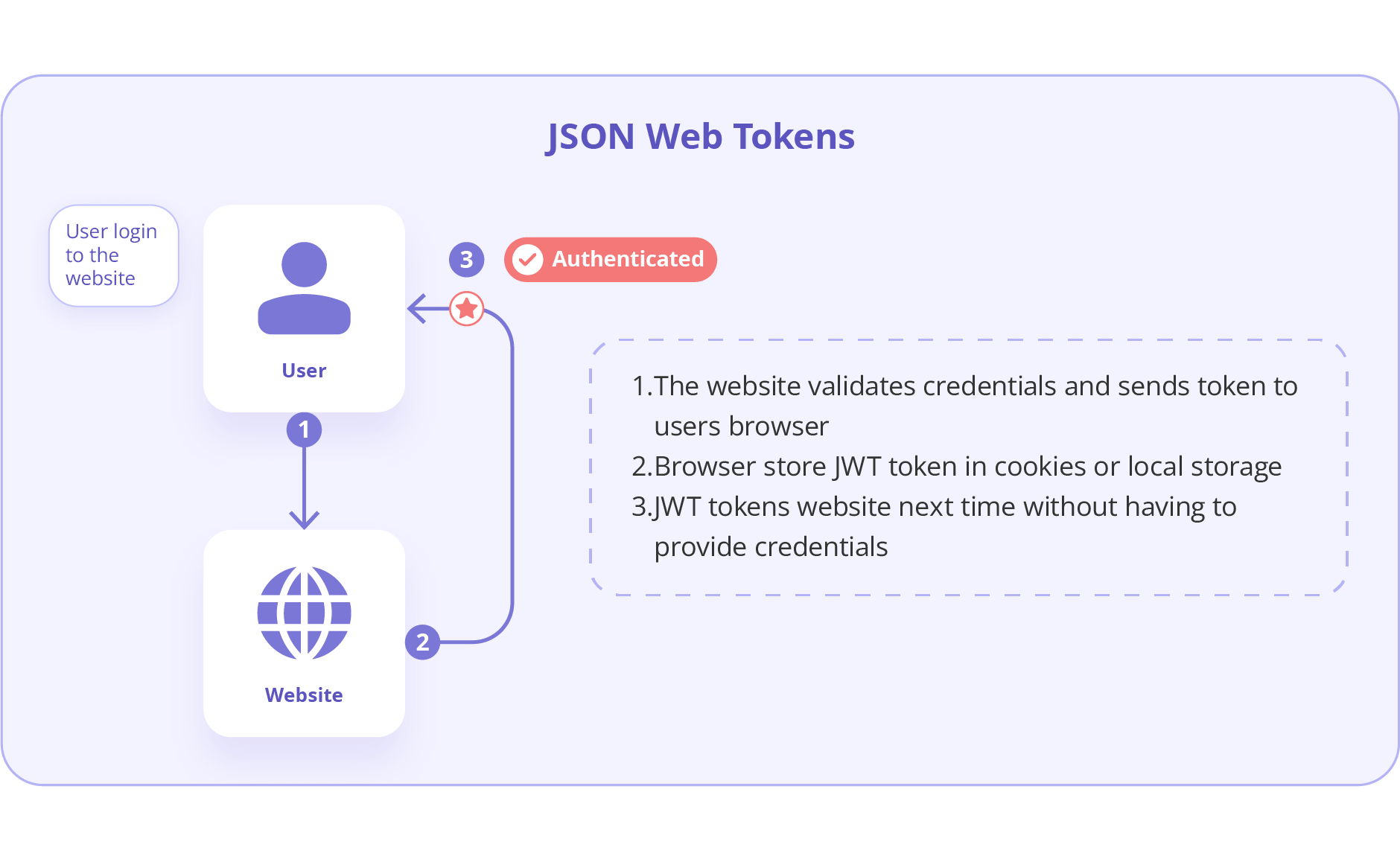
The implementation of modern authentication methods, such as OAuth 2.0 and JWT, can significantly improve API Gateway Authentication practices in the system. In fact, OAuth 2.0 is popular for its ability to allow third-party access to resources without exposing credentials. Also, JWT tokens provide a secure and URL-safe means of communication between parties.
Also Read, API without Authentication
Encrypt Sensitive Data
Sensitive data, both at rest and in transit, should be encrypted to prevent eavesdropping or tampering by unauthorized parties. Moreover, APIs should use protocols such as SSL/TLS. And also ensure that the API Gateway communicates with clients over HTTPS, exemplifying API Gateway Encryption.
Validate API Requests
User inputs need to be validated to prevent malicious users from transmitting malicious data or code through the API Gateway.
Monitoring and Logging
It is crucial to log the activity of the API Gateway to track client requests, access, and execution. This provides valuable insights in case someone tries to exploit any vulnerabilities around the API Gateway.
Implement Rate Limiting
Rate limiting is a useful method for API Gateway security. It helps to prevent common attacks on the API Gateway. This includes Denial of Service (DoS) attacks by avoiding the API Gateway from being overwhelmed by client requests and resulting in errors. In fact, rate limiting can be based on factors such as IP address, API key, and request frequency.
Use Cloud-Based API Gateways
Cloud-based API Gateways provide advanced security features and scalability compared to in-house API Gateways. Also, they offer a range of features that can improve performance and ensure the security of the API Gateway.
How to Secure an API with Cloud Solutions?
- Securing AWS API Gateway: Leverage AWS’s native features such as IAM roles and security groups to enhance your API’s security posture.
- Cloud-based API security management: Utilizes scalable security measures that adapt to your API’s demand without compromising on security.
Also Read, API Security Testing and its Best Tools
Enable a Web Application Firewall (WAF)
Protecting the API Gateway with a web application firewall (WAF) is an effective way to secure the API and its Gateway. A WAF restricts access to APIs based on a set of predefined conditions and rules, securing the Gateway from common threats and vulnerabilities.
Benefits of API Gateway Security
It provides numerous benefits to the security of API in different ways. In fact, one of the best ways it helps is by enhancing the security of microservices and by improving API Gateway Authentication and API Gateway Encryption capabilities.
Enhanced Microservices Security
API Gateways provide an added layer of security to microservices by making it difficult for attackers to reach and compromise them. This is because the API Gateway shields the underlying infrastructure of the microservices in its backend.
Improved Authentication and Authorization
Efficient enforcement of authentication and authorization policies ensures that no unauthorized users gain access to the APIs and underlying systems.
Protection of Sensitive Data
By acting as an intermediary, the API Gateway protects sensitive data transmitted via APIs from unauthorized access.
Defense Against Attacks
API Gateways serves as a formidable barrier against a wide range of attacks, including SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF), from reaching the services and data in its backend.
Also Read, Best API Security Testing Tools
Compliance
Organizations can easily comply with regulatory and industry API Gateway Compliance requirements related to data security and privacy by using an API Gateway.
Also Read about, API Security Trends of 2025
Concluding API Gateway Security Features
API gateways act as a middle layer between clients and backend services, offering various security features to protect APIs and the underlying systems. Here are some key security features of API gateways:
Authentication and Authorization
- Centralized authentication: Integrate with external authentication providers like OAuth or OpenID Connect to manage user identities and access control.
- API key management: Issue unique API keys to authorized users or applications for access control.
- Resource policies: Define fine-grained access control rules for specific API resources and methods (e.g., GET, POST, PUT, DELETE).
- Authorization with IAM: Leverage Identity and Access Management (IAM) for role-based access control to your API resources.
- Lambda authorizers: Use serverless Lambda functions for custom authorization logic based on specific requirements.
Data Security
- HTTPS enforcement: Enforce secure communication over HTTPS to encrypt data transmission between clients and the API gateway.
- Input validation: Validate request parameters to prevent malicious code injection attempts like SQL injection or cross-site scripting (XSS).
- Data masking: Mask sensitive data in API responses to prevent unauthorized access to confidential information.
Traffic Management
- Rate limiting and throttling: Limit the number of API requests per user, IP address, or other criteria to prevent denial-of-service (DoS) attacks and control resource usage.
- Web application firewall (WAF) integration: Integrate with a WAF to filter out malicious traffic and protect against common web application vulnerabilities.
Monitoring and Logging
- API request and response logging: Log all API requests and responses for auditing purposes and to identify suspicious activity.
- Monitoring and analytics: Monitor API usage patterns and performance metrics to detect anomalies and potential security threats.
By implementing these security features, API gateways can significantly enhance the security posture of APIs and backend services, ensuring authorized access, data protection, and overall API health.
Adoption of Zero Trust Architecture
Incorporate the concept of zero-trust architecture in relation to API gateways. Explain how Zero Trust principles can be applied to API security by default denying access until trust is explicitly verified. This approach is crucial as organizations move towards more decentralized IT environments.
Advanced Threat Detection Systems
Discuss the integration of advanced threat detection systems with API gateways. Highlight the use of machine learning and behavioral analytics to detect unusual patterns that may indicate a breach or an attempted attack. These systems can provide an additional layer of security by identifying threats that are not caught by traditional methods.
API Security Posture Management
Introduce the concept of API Security Posture Management (ASPM). ASPM provides continuous analysis and auditing of API configurations and permissions to ensure they meet security standards, helping to prevent misconfigurations and vulnerabilities.
Integration with DevSecOps
Emphasize the integration of API Gateway security practices within DevSecOps workflows. Discuss how API security can be automated and monitored continuously to ensure it keeps pace with rapid deployment cycles in a DevSecOps environment.
Geographic Restrictions and Data Sovereignty
Address the implementation of geographic restrictions through API gateways to comply with data sovereignty laws and regulations. This can be crucial for multinational organizations that need to manage data localization requirements effectively.
Why API Gateways are critical security enforcers in a zero-trust world?
In a zero-trust environment, trust is never assumed; each API request is authenticated, authorized, and continuously verified, regardless of its origin. API gateways enforce these policies at the front line: authenticating requests, applying granular access controls, and integrating with threat intelligence to prevent unauthorized or risky activity, making them vital for robust, proactive security.
- Understanding the Role of an API Gateway in Modern Architectures
An API Gateway acts as a single entry point for client requests, handling routing to the correct backend service, enforcing authentication and authorization policies, and applying rate limiting to manage traffic and prevent system overload.
It streamlines communication, secures access, and ensures reliable API usage across microservices Central point for observability, enforcement, and compliance.
Central point for observability, enforcement, and compliance
The API Gateway centralizes monitoring, capturing logs and metrics for every API transaction. It enforces security and usage policies consistently, providing a unified location for compliance controls, analytics, and real-time alerts. This simplifies observability and helps organizations maintain regulatory and operational standards across all API interactions.
- TLS, Encryption & Secure Communication
Enforce HTTPS and TLS 1.3
Always enforce HTTPS and require TLS 1.2 or higher—ideally TLS 1.3, which offers stronger security and faster performance—to protect data in transit from eavesdropping or tampering. Use security headers like HSTS to reject all HTTP traffic and ensure strict HTTPS compliance.
Mutual TLS (mTLS) between services:
Implement mutual TLS (mTLS) for service-to-service communication. This enforces that both parties authenticate each other using certificates, preventing unauthorized access and securing internal API calls end to end.
What TLS versions should API Gateway support?
Modern security standards recommend supporting only TLS 1.2 and TLS 1.3. Avoid enabling legacy versions like TLS 1.0 to eliminate known vulnerabilities, and configure your gateway to use only strong cipher suites for maximum protection.
- Authentication & Authorization Strategies
OAuth 2.0, JWT, RBAC — defined and compared
OAuth 2.0 delegates user consent and access via tokens. JWTs (JSON Web Tokens) carry identity and claims for stateless authentication. RBAC (Role-Based Access Control) grants permissions based on user roles. OAuth 2.0 often uses JWTs for access, while RBAC defines what resources those tokens can access.
Internal vs. external identity providers:
Internal identity providers are managed in-house, like LDAP or custom databases. External providers offer third-party authentication, such as Google, Azure AD, or Auth0, and simplify integrations across platforms. API Gateways can support either, letting organizations choose what fits their needs.
How does API Gateway enforce authentication securely?
The API Gateway enforces authentication by validating credentials or tokens (OAuth, JWT, API keys) before forwarding requests. It checks token integrity and expiration, integrates with identity providers, and denies unauthorized access at the edge, keeping internal services protected.
- Token, Key & Certificate Lifecycle Management
(New Section – Filling a gap)
API key security, JWT rotation best practices
Rotate API keys at least every 90 days, after incidents, or when staff changes occur. Automate key rotation to minimize human error and reduce exposure to leaked or compromised keys. For JWTs, use short expiration times and ensure frequent re-issuance to limit token misuse.
Automated certificate issuance & renewal
Automate certificate management to handle issuance and renewal without service interruptions. Use trusted tools or integrated platforms to avoid downtime, expired certificates, and manual mistakes.
Automated API Key Rotation in API Gateway
Leverage automated key rotation features in your API Gateway or connected key management systems. Ensure new API keys are provisioned and validated before deactivating old ones, guaranteeing seamless transitions and uninterrupted access.
- Rate Limiting, Throttling & Circuit Breakers
(Enhancement of “Advanced Threat Detection”)
Configuring burst controls and fair usage limits:
API Gateways enforce rate limits and burst controls to prevent abuse and ensure fair resource use. Rate limits restrict how many requests a client can send per second or minute, while burst controls allow short spikes in traffic up to a defined maximum before throttling kicks in, returning 429 errors when exceeded.
Circuit breaker patterns for resilient backends:
A circuit breaker pattern helps protect backend services by automatically rejecting or delaying new requests when repeated failures occur. This prevents overloading struggling systems, allowing time for recovery and maintaining overall API reliability.
Can API Gateway act as a circuit breaker during backend failures?
Many API Gateways can function as a circuit breaker by monitoring backend health and throttling or blocking requests when a backend becomes unresponsive or starts failing. This limits cascading failures and helps maintain a stable API ecosystem.
- Input Validation & Schema Enforcement
(New Section – Fills critical missing gap)
JSON schema validation, size limits, format enforcement:
API Gateways can enforce JSON schema validation to ensure request and response payloads strictly match defined structures and data types, rejecting invalid data early. You can also set size limits and format constraints in the schema, protecting against oversized or malformed payloads and ensuring data integrity.
Protecting upload endpoints and sanitizing input:
To secure upload endpoints, combine strict input validation with file size checks and format verification. API Gateways should reject files or data that do not meet defined criteria and sanitize inputs to block malicious content, reducing injection and overflows risks.
API Gateway Input Validation JSON Schema Size Limit:
Using API Gateway’s built-in JSON schema validation, you can automate validation and reject requests exceeding configured size or schema limits, providing a simple way to enforce payload standards and prevent excessive or unsafe data from reaching backend services.
- WAF & Bot Protection
(Can be added under or near Threat Detection)
Integrate WAF to block SQLi, XSS, L7 DDoS
A Web Application Firewall (WAF) sits in front of your API Gateway, filtering traffic to block threats like SQL injection, cross-site scripting (XSS), and Layer 7 DDoS attacks.
WAF rules analyze request patterns and payloads, and only safe traffic is forwarded to the backend, stopping many attacks before they reach your API.
Real-time bot traffic mitigation
WAFs can block or challenge malicious bots using IP reputation, behavior analysis, and custom rules—protecting APIs from credential stuffing, scraping, and automated abuse.
How to integrate WAF with API Gateway to block SQLi/XSS?
- Cloud and commercial gateways like AWS, Azure, or Alibaba Cloud allow you to attach WAF policies directly to API Gateway instances or routes.
- Define WAF rules to detect and block SQLi/XSS patterns, either using managed rule sets (such as OWASP CRS) or by creating custom policies.
- All incoming traffic is evaluated against these rules before reaching your APIs, and malicious requests are automatically blocked with denial responses like HTTP 403.
- For example, in AWS, associate a WAF web ACL to an API stage from the API Gateway console and enable relevant security rules to filter SQLi/XSS threats before they impact your backend.
- Secure API Versioning & Deprecation
Best practices to retire old versions without disruption:
Adopt clear versioning in API paths or headers and notify developers early about deprecation timelines. Redirect traffic from old to new versions where possible, and provide extensive documentation to support smooth migration, minimizing service disruption for users.
Monitoring deprecated endpoints:
Continuously monitor traffic to deprecated endpoints with logging and analytics. This helps identify active consumers, track migration progress, and detect any unauthorized or risky usage before fully disabling old APIs.
API Gateway deprecation strategy secure versioning:
A secure deprecation strategy via API Gateway involves gradually phasing out old versions with clear communication, analytical tracking, and controlled endpoint shutdowns. Enforcing strict versioning ensures only supported and secure API endpoints remain accessible.
- Service-to-Service Security & Zero Trust Implementation
Use of mTLS and internal tokens for microservice security:
Mutual TLS (mTLS) enforces two-way authentication between microservices, ensuring both sides present valid certificates before communication starts. This encrypts service-to-service traffic and restricts connections to trusted entities, protecting against unauthorized access and interception. API Gateways with mTLS support can automate certificate management and simplify secure microservice integration.
No implicit trust – Identity at every hop:
In a Zero Trust Architecture, no request is trusted by default. Each request, whether internal or external, must prove identity at every hop using certificates (mTLS) or internal tokens. API Gateways validate these identities before forwarding any request, ensuring strict authentication and authorization continuously across the service mesh.
mTLS between services api gateway zero trust
With mTLS on API Gateways, every service call is authenticated and encrypted, which enforces zero trust by verifying identities and rejecting any unapproved requests. This minimizes attack surfaces and fulfills compliance needs, creating a robust foundation for secure, scalable microservice environments.
- Security Observability: Monitoring, Logging, & SIEM
Real-time logging, anomaly detection, audit trails
Integration with SIEM systems like Datadog, Splunk, ELK
Threat modeling and breach visibility
- Geographic Restrictions & Data Sovereignty
(Refine your existing section)
Regional access control via geofencing
API Gateways can use geofencing to enforce where API traffic comes from by defining virtual geographic boundaries—such as countries, states, or cities. Requests originating outside allowed regions can be blocked or redirected by matching a request’s source IP to geofence rules, ensuring regional access control and supporting data sovereignty requirements.
Legal compliance (GDPR, CCPA, etc.)
Restricting data flows to specific regions helps you comply with laws like GDPR and CCPA. By keeping sensitive data within designated jurisdictions and preventing unauthorized cross-border transfers, you reduce compliance risk and meet regulatory obligations.
How do I enforce regional access with geofencing rules?
- Define geographic boundaries using latitude, longitude, radius, or polygons in your geofencing API.
- Integrate with the API Gateway to match each incoming request’s location (via IP geolocation) against these boundaries.
- If a request falls outside approved regions, the API Gateway can automatically block, redirect, or respond with a compliance error message, enforcing your geolocation access policies
- Compliance-Ready Gateway Security
Align with PCI-DSS, HIPAA, GDPR
API Gateways help enforce compliance by securing sensitive data (PCI-DSS), protecting health information (HIPAA), and upholding privacy rights (GDPR) through strong authentication, encryption, data minimization, and consent management. Built-in controls support user rights, breach reporting, and automated data handling policies.
Checklist-based enforcement:
Integrate compliance checklists directly into API deployment processes. Use schema validation, access controls, encrypted communication, and automated consent checks to systematically enforce policy requirements at the gateway level.
Audit logging and reporting readiness:
Maintain immutable logs of all API access, data changes, and security events. Enable on-demand reporting to support audits, demonstrate compliance, and quickly investigate incidents involving regulated data.
- DevSecOps Integration: Automating Gateway Security
CI/CD security injection:
Integrate security checks into your CI/CD pipelines to automate scanning for vulnerabilities, enforce policy compliance, and run API security tests on every build and deployment. This ensures APIs are reviewed and protected at every stage without manual intervention.
IaC templates for consistent API Gateway policy deployment:
Use Infrastructure as Code (IaC) tools like Terraform or CloudFormation to define and deploy API Gateway policies—such as rate limits, authentication, and encryption settings—ensuring every environment inherits consistent, secure configurations.
Secrets management and environment isolation:
Store sensitive information (keys, tokens, certificates) in dedicated secrets management systems rather than code or configs. Isolate environments (dev, test, prod) using separate credentials and access policies, preventing leaks and cross-environment risk.
Conclusion
Securing API Gateways is a core installation that helps to keep the API secure. Therefore, securing the API from attacks is very important. Ensuring API gateway security can provide improved security for microservices by ensuring the authenticity of traffic coming in, authorization of various API functions, and protecting sensitive data in the API and its underlying systems. To summarise, some of the API gateway security best practices are using modern authentication methods, encrypting sensitive rate limiting, using cloud-based API gateways, and enabling a web application firewall (WAF).
Interested in API Security?
The Practical DevSecOps’s Certified API Security Professional (CASP) course is an industry-recognized certification to specialize in API security. This certification provides hands-on training through browser-based labs, 24/7 instructor support, and the best learning resources.
Most Frequently Asked Questions
What are the key features of a secure API Gateway?
Secure API Gateways typically include centralized authentication, encryption, rate limiting, detailed logging and monitoring, and integration with identity providers for OAuth and JWT-based access control.
How does API Gateway security benefit my application?
API Gateway security enhances data protection, strengthens access control, supports regulatory compliance, and provides a robust defense layer against external threats, ensuring reliable and secure application performance.
What are the most common threats to API Gateways?
The most common threats include SQL injection, cross-site scripting (XSS), denial-of-service (DoS) attacks, credential stuffing, and unauthorized access through misconfigurations.
How can I implement OAuth 2.0 for API Gateway authentication?
To implement OAuth 2.0, configure your API Gateway to accept and validate access tokens provided by an OAuth 2.0 authorization server, managing authentication and resource access based on defined scopes and roles.
What are the best tools for monitoring API Gateway security?
Effective tools for monitoring API Gateway security include AWS CloudWatch, Datadog, Splunk, and New Relic, which provide capabilities for real-time monitoring, logging API traffic, and detecting anomalous activities.
How do I set up rate limiting on an API Gateway?
To set up rate limiting, use the API Gateway’s management tools or configuration settings to define limits based on IP address, user ID, or request frequency to prevent abuse and manage traffic efficiently.
What are the advantages of using cloud-based API Gateways?
Cloud-based API Gateways offer scalability, enhanced security features, built-in compliance with industry standards, easier integration with existing cloud services, and reduced maintenance overhead.
How does a Web Application Firewall (WAF) enhance API Gateway security?
A Web Application Firewall (WAF) protects against common web exploits and vulnerabilities by filtering and monitoring HTTP traffic to and from an API Gateway based on pre-defined security rules.
What are the compliance requirements for API Gateways?
Compliance requirements for API Gateways commonly include adhering to data protection regulations like GDPR and HIPAA, ensuring secure data transmission standards, and implementing robust access control and encryption practices.
How can I ensure continuous security for my API Gateway in a DevSecOps environment?
To ensure continuous security, integrate security practices within the CI/CD pipeline by automating security tests, regularly updating security protocols, and using real-time monitoring tools to continually assess and improve the security posture of your API Gateway.
Can API Gateway Upload More Than 10MB?
No, API Gateway has a hard limit of 10MB for payload size. This limit can not be increased, but there are several workarounds to handle larger file uploads:
Use Amazon S3 Pre-signed URLs
API Gateway can return a pre-signed URL for Amazon S3, allowing clients to upload files directly to S3 without going through API Gateway. This bypasses the 10MB limit and enables uploads up to 5TB using multipart uploads.
Multipart Uploads
Amazon S3 supports multipart uploads, which can handle files larger than 5GB. This involves splitting the payload into multiple segments and sending separate requests for each part.
API Gateway as a Proxy
API Gateway can be used as a proxy to generate a pre-signed URL for Amazon S3. This approach involves making a request to API Gateway, which then generates the pre-signed URL and returns it to the client. The client then uses this URL to upload the file directly to S3.
How to secure API Gateways and API Endpoints?
To secure API gateways and endpoints, implement strong authentication and authorization mechanisms, such as OAuth or API keys. Use HTTPS to encrypt data in transit and employ rate limiting to prevent abuse. Regularly update and patch API software to mitigate vulnerabilities. Additionally, use threat detection and response strategies, and conduct thorough API security testing, including penetration testing and vulnerability assessments. Finally, apply security policies consistently across all APIs to ensure comprehensive protection.
What’s the easiest way to rotate JWTs automatically?
The simplest way is to use a JWKS (JSON Web Key Set) endpoint for dynamic public key rotation. Your API Gateway can fetch new signing keys automatically from this endpoint, allowing you to update keys without manual changes or service downtime, ensuring seamless and secure JWT verification.
How to block bots and L7 DDoS with API Gateway?
API Gateways can block bots and Layer 7 DDoS attacks by integrating with a Web Application Firewall (WAF), which uses rules to detect and block malicious requests. Features like rate limiting, IP blocking, and behavioral analysis further help stop automated abuse and traffic floods before they reach your backend.
Why is the least privilege important in API Gateways?
Enforcing least privilege ensures each client, user, or service only has access to the minimum resources needed. This reduces attack surfaces, prevents unauthorized data exposure or system changes, and limits the impact of compromised credentials or vulnerabilities within your API ecosystem.
Also Read, Best API Security Books
Download the Free E-book on API Security




